ISO27001 Certification Services
ISO 27001 is a global standard that gives a structure for setting up, operating, keeping, and enhancing an Information Security Management System (ISMS). An ISMS is a collection of rules, processes, and controls that try to safeguard the secrecy, completeness, and accessibility of information assets from different dangers and risks. ISO 27001 assists organizations of any size and sector to manage their information security in a methodical and coherent way.
ISO27001 Certification Benefits
- Enhancing the protection and resilience of information assets against cyberattacks, data breaches, natural disasters, human errors, and other incidents.
- Improving compliance with legal, regulatory, contractual, and customer requirements related to information security.
- Increasing the trust and confidence of customers, partners, suppliers, investors, and regulators in business’s ability to manage information security.
- Reducing the costs and impacts of information security incidents and improving recovery capabilities.
- Improving the efficiency and effectiveness of information security processes and controls.
- Supporting the achievement of strategic goals and objectives by aligning information security with business needs and risks.
- Enhancing the reputation and competitiveness of Business’s in the market.
- Creating a culture of information security awareness and responsibility among the employees and stakeholders.
An ISMS consists of four main components
- The context of the organization: This component involves understanding the internal and external factors that affect information security, such as the organizational structure, culture, strategy, objectives, stakeholders, legal and regulatory obligations, and risks and opportunities.
- The leadership and commitment: This component involves establishing the information security policy, roles, and responsibilities, and ensuring the support and involvement of the top management and the relevant stakeholders in the ISMS.
- The planning and operation: This component involves identifying the information security objectives and the actions to achieve them, such as conducting risk assessment and treatment, selecting, and implementing the appropriate controls, and monitoring and measuring the performance and effectiveness of the ISMS.
- The evaluation and improvement: This component involves reviewing and auditing the ISMS to ensure its suitability, adequacy, and effectiveness, and identifying and implementing the opportunities for improvement, such as corrective and preventive actions, and continual improvement.
ISMS implementation process can be divided into six phases
- The initiation phase: This phase involves defining the scope, boundaries, and objectives of the ISMS, and obtaining the approval and support from the top management and the relevant stakeholders.
- The planning phase: This phase involves conducting a gap analysis to identify the current state and the desired state of the ISMS and developing a project plan and a risk management plan to guide the implementation process.
- The implementation phase: This phase involves executing the project plan and the risk management plan, and establishing and documenting the ISMS policies, procedures, and controls.
- The operation phase: This phase involves operating and maintaining the ISMS policies, procedures, and controls, and ensuring their alignment with the changing business needs and risks.
- The monitoring phase: This phase involves measuring and evaluating the performance and effectiveness of the ISMS policies, procedures, and controls, and reporting and communicating the results and feedback to the top management and the relevant stakeholders.
- The review and improvement phase: This phase involves conducting internal and external audits to verify the compliance and conformance of the ISMS with the ISO 27001 standard and Business requirements, and identifying and implementing the opportunities for improvement, such as corrective and preventive actions, and continual improvement.
Some of the best practices and challenges of ISO 27001 implementation are:
- Obtaining commitment and support from the top management and the relevant stakeholders throughout the ISMS implementation process.
- Setting the ISMS objectives and scope to match business requirements and risks.
- Adopting a risk-based approach to identify and prioritize information security threats and vulnerabilities, and to select and implement the appropriate controls.
- Integrating the ISMS with the existing management systems and processes of Business’s , such as quality, environmental, health and safety, and business continuity.
- Establishing a clear and consistent documentation and communication system for the ISMS policies, procedures, and controls.
- Providing adequate resources, training, and awareness for the ISMS implementation and operation.
- Monitoring and measuring the ISMS performance and effectiveness using relevant indicators and metrics.
- Conducting regular reviews and audits to ensure the ISMS compliance and conformance with the ISO 27001 standard and Business requirements.
- Implementing a continual improvement process to identify and address the gaps and opportunities for the ISMS enhancement challenges.
- Lack of awareness and understanding of the ISO 27001 standard and its benefits among the top management and the relevant stakeholders.
- Resistance to change and lack of cooperation from the employees and stakeholders in the ISMS implementation and operation.
- Complexity and diversity of information security risks and requirements across the organization.
- Limited resources, time, and budget for the ISMS implementation and operation.
- Difficulty in selecting and implementing suitable controls for the information security risks and requirements.
- Difficulty in establishing and maintaining the ISMS documentation and communication system.
- Difficulty in monitoring and measuring the ISMS performance and effectiveness.
- Difficulty in achieving and maintaining the ISMS compliance and conformance with the ISO 27001 standard and the organizational requirements.
- Difficulty in implementing a continual improvement process for the ISMS enhancement
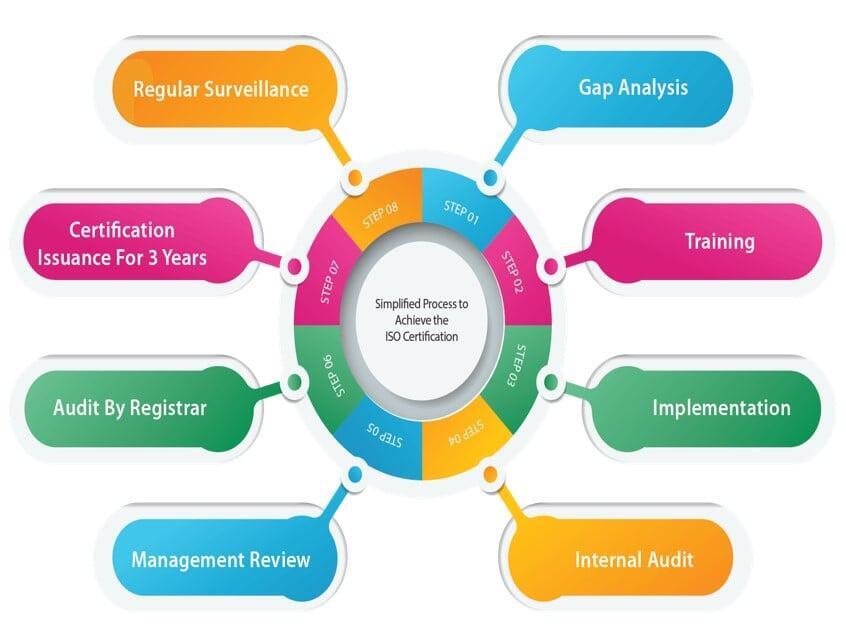
Workflow Diagram
This workflow diagram illustrates the main steps and activities involved in each phase of the ISMS implementation process, as well as the inputs and outputs of each phase. The workflow diagram is based on the Plan-Do-Check-Act (PDCA) cycle, which is a widely used model for managing and improving processes and systems.
ISO27001 Process & Certification Flow
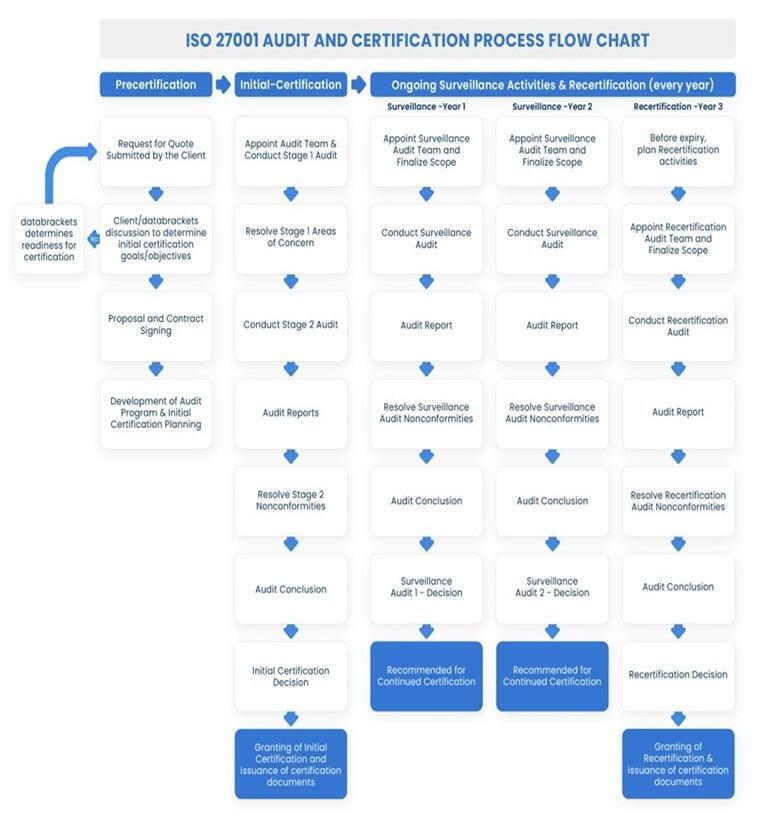
In Conclusion
- ISO 27001 is an international standard that provides a framework for establishing, implementing, maintaining, and improving an information security management system (ISMS).
- An ISMS is a set of policies, procedures, and controls that aim to protect the confidentiality, integrity, and availability of information assets from various threats and risks.
- ISO 27001 helps organizations of any size and sector to manage their information security in a systematic and consistent way.
- ISO 27001 offers many benefits for organizations and stakeholders, such as enhancing the protection and resilience of information assets, improving the compliance with legal, regulatory, contractual, and customer requirements, increasing the trust and confidence of customers, partners, suppliers, investors, and regulators, reducing the costs and impacts of information security incidents, improving the efficiency and effectiveness of information security processes and controls, supporting the achievement of strategic goals and objectives, enhancing the reputation and competitiveness of the organization, and creating a culture of information security awareness and responsibility.
- ISO 27001 implementation involves four main components: the context of the organization, the leadership and commitment, the planning and operation, and the evaluation and improvement.
- ISO 27001 implementation can be divided into six phases: the initiation, the planning, the implementation, the operation, the monitoring, and the review and improvement.
- ISO 27001 implementation requires a workflow diagram that illustrates the main steps and activities involved in each phase, as well as the inputs and outputs of each phase.
- ISO 27001 implementation also requires following some best practices and overcoming some challenges, such as obtaining the commitment and support from the top management and the relevant stakeholders, aligning the ISMS objectives and scope with the business needs and risks, adopting a risk-based approach, integrating the ISMS with the existing management systems and processes, establishing a clear and consistent documentation and communication system, providing adequate resources, training, and awareness, monitoring and measuring the ISMS performance and effectiveness, conducting regular reviews and audits, and implementing a continual improvement process.
